Cyber crime started as a hobby. Now it is an organized business, of which the consequences can be of negative influence to your organization. Not only are we talking about fines and reputation damage, but also cost loss due to the aftermath of a possible data leak.
It’s your task of a CISO to identify all safety risks. How can these risks be limited and how do you ensure that the safety standards within the organization are widely observed?
And that's not all, because your employees actually form the biggest risk. The human factor when processing (sensitive) information turns out to be the biggest cause of a data leak.
Checking upon email security is therefore not a nice-to do, but a must do. If risks can be limited in this area, then this is one stumbling block that you as a data security authority no longer have to worry about. But, how exactly can it help you? We have 5 tips for you:
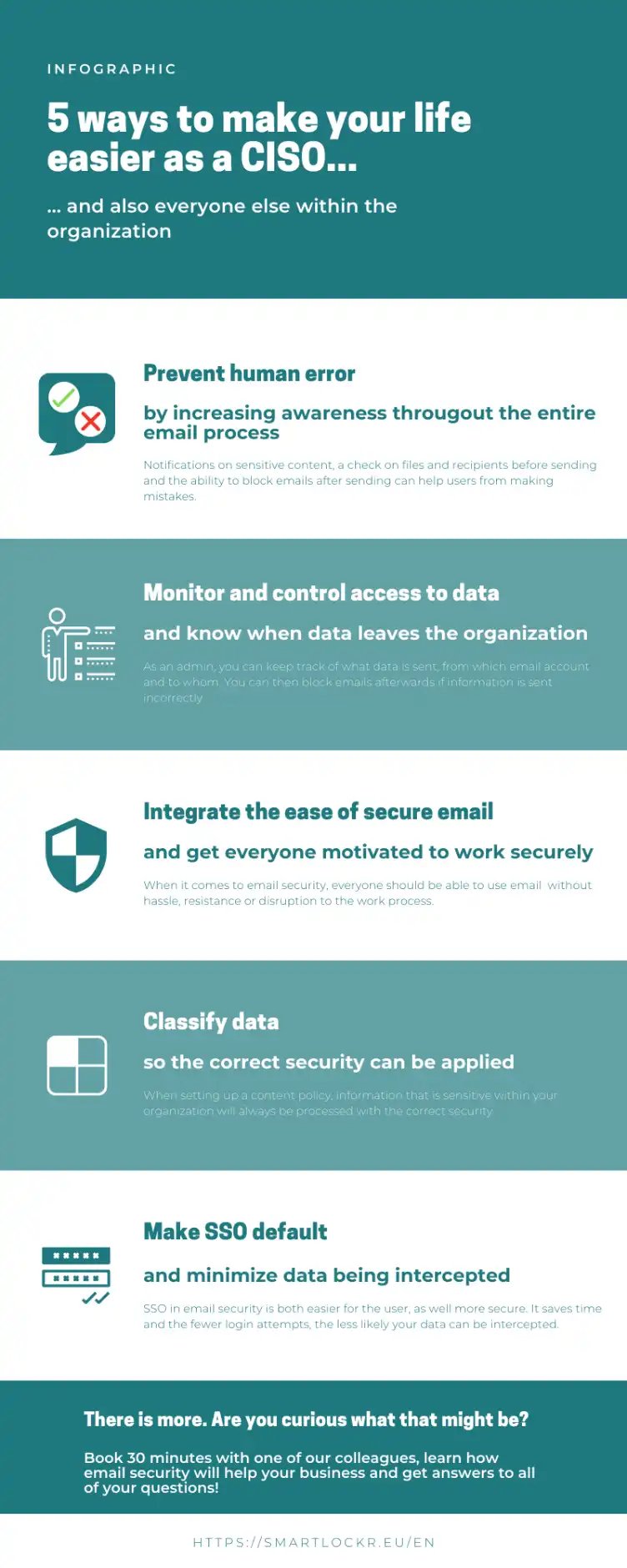

5 ways to make your life as an CISO easier
1. Data loss because of unsafe email
Losing sensitive data is not necessarily something that only happens from external factors. In many cases it is not a cyber attack or phishing attack with malware. As indicated, human error is the biggest factor when it comes to data loss. Sending information to the wrong recipient resulted in a data leak in 74% of cases.
But preventing information being sent to the wrong recipient, is actually something you can keep control of.
The right email solution ensures that the user processes information correctly.
2. Manage and monitor access to data
Is someone no longer working for the organization? Make sure to block all login details to prevent someone from accessing all sensitive information, even after leaving the organization. It seems obvious, but it often happens that ex-employees still have access to the inbox of their previous email account.
From an admin portal, you should be able to easily track what is leaving the organization, from which email account and what exactly has been shared. That’s not all: for complete control it is important that you as an administrator also have the option to block accounts and actions.
Has information left the organization? Then it should be possible to block this information.
3. Integration of user-friendliness in secure email will motivate to work secure
Once you have mapped all risks, gathered insights and know where all the data goes, it is important to get an overview of this. Having the right software is one thing, but making sure they are working and used properly is the second. Of course you don’t want to implement software, which won’t be used in the way it is supposed to.
When it comes to email security, all users should be able to work with it. Without any hassle, resistance or disruption to the work process. After all, this is one goal: to implement a secure work process in which incoming and outgoing data is securely monitored.
An email solution must therefore also be user-friendly. Is the email environment easy to navigate in? Can secure email be enabled easily? Your employees will easily adapt to the situation, if the situation is clear and working with a system is user-friendly.
4. Classification of data
Not all data is equally valuable. There is a difference between processing customer data via email or discussing the location for the next staff party. But, how do you get a grip on what kind of data is processed and when? As an organization it is important to make a distinction here, to be able to make an inventory how and which data is processed.
When it comes to email, the ability to classify content gives you this option. An example: if you work for a healthcare organization, it’s good to look at options in which sensitive health information is processed correctly (or the standards of the NTA 7516). This may involve the exchange of patient files or status overviews of patients.
An email solution that implements this with a content policy will be able to offer the appropriate security for this. Recognizing sensitive information helps the user in the email process. You as an administrator can set this up, so the information you classify as sensitive is always sent with the right security, like one- or two-factor-authentication.
5. Make SSO (Single Sign On) the standard within the organization
Those who don’t use SSO yet, are actually leaving many doors open for cyber criminals. Every time a user has to log in to a system, there is the risk of data being intercepted. Why would we want to make things easy?
SSO (Single Sign On) in email security is both easier for the user and more secure. The advantages? The convenience is for the user. Logging in and working on various systems is done in a very user-friendly way and saves a lot of time. The same comes for safety.
The fewer login attempts there are, the less chance there is for unauthorized persons to access the systems
How Smartlockr could make your life easier as a CISO
These are just 5 tips that will help you find the right email security. But there's more. Do you want to know which functionalities can help your organization? Then book your demo and discover in only 30 minutes how the risks in email security can be reduced.

