Preventing data breaches should be a simple task, not a day job!
Most data breaches are caused by human error. By making the process simple, less mistakes will be made. But what is a data breach? What should you do after you've experienced a data breach? And more importantly: how do we make sure that we prevent data breaches in the future. Let's dive in!

When you think of a data breach, we typically think of hackers gaining access to our data and selling it on the dark web. Everyone can probably recall a hacking incident of the past year or so, but data breaches are not just about thieves working in the night out to steal your data.
If we want to get technical about it a data breach is a security breach which exposes confidential or protected information, whether by accident or deliberate. A data breach is also about more than just losing personal data.
Did you know these examples also count as data breaches?
- Confidentiality breach: Sending personal information to the wrong recipient;
- Integrity breach: Altering personal data without permission;
- Availability breach: Loss of availability of personal data.
Generally, data breaches happen because of two main factors: either your technology isn't protected enough, or your users have slipped up. We can identify the five most common types of data breaches below:
Human error
Not every breach is caused by malicious intent, sometimes humans make mistakes that lead to a data breach.
Phishing
Phishing is the practice of sending emails that look exactly like that of a reputable company to get you to click on links and forfeit your personal information.
Physical security breach
Not everything comes down to digital cyber security crimes, sometimes personal information is stolen like grabbing a USB off someone's desk or stealing a laptop.
Ramsomware or malware
Ransomware is when your computer is suddenly being held ‘hostage’ and encrypted, you usually pay a fee before the hackers decrypt it. Malware is your old and trusted viruses of the past or, talking in more modern terms, ‘keylogging’ is a good example of it.
Criminal hacking
Someone illegally smashes through your security system and hacks it.
One of these causes is not like the others... You guessed it, human error! According to IBM, human error was a contributing factor in 95 percent of all data breaches. Researchers from Stanford University found that it was approximately 88 percent, staggering numbers indeed! Especially if you consider that the average cost of a data breach is 4.4 million dollars...
95%
of data breaches are due to human error, according to IBM's study.
Real life examples of human error that caused data breaches include:
In August 2018, an employee of the Strathmore Secondary College in the United States accidentally published 300 student records on the school's intranet which could be viewed by all students and their parents.
In 2018, the personal information of around 21,500 Marines, sailors and civilians was exposed because the US Department of Defense sent out an unencrypted email to the wrong distribution list.
In April 2022, the University Medical Center Groningen in the Netherlands accidentally leaked all email addresses of men experiencing urinary problems by CC’ing all of them in a request for additional information.
So what exactly do we count as human error?
When we're talking about human error in cyber security, it gains a new (and more serious!) meaning: it's the unintentional actions, or lack thereof, of end users that cause a security breach. Of course, these errors could be anything from falling for a phishing scheme to sending sensitive information to the wrong recipient, usually unintentionally.
So why does it happen? People have to navigate complex, and at times tiresome, security measures. Think of all the different plugins and programs that you yourself have to use! Password generators, two-factor authentication, complex navigation... It isn't easy to stay safe sometimes! Throw in a demanding job and you've got a stressed Sandra on your hands.
The problem is that when these complexities add up, people can do two things: they end up making a mistake or people may start to work around these complex solutions. Both can lead to a data breach.

Generally speaking, human error can usually be divided into two ‘types’ of error, namely: skill-based error and decision-based errors.
-2-2.png?width=511&height=544&name=Presentation%20format%20(13)-2-2.png)
Skill-based errors
Skill-based human error usually consists of mistakes that happen when you're ‘just doing your job'. You know how to do it correctly, but you've still made a small mistake. You slip up because you might be tired or too busy to pay close attention.
Any email security worth their salt should always work in the background without needing activation to decrease these mistakes!

Decision-based errors
Decision-based human error happens when a user makes a wrong decision. Maybe they're just not aware of the right procedures, or maybe they make an active decision to work around your complex solution.
Increasing the awareness of your users that alerts them to their errors in judgment will likely decrease these decisions.
The most common factors in human error:
Now that you're aware of the two most common types of errors, what's really behind some of these errors? We can demystify the causes behind human error through a few reasons:
A lack of awareness
People simply don't know what to do or where they go wrong.
Overconfidence
A user has done this so many times that it becomes a routine task, they can't go wrong. Until they do go wrong.
Read more - Human factor in data security: Confident Carla
Poorly designed systems
People will work around a complex solution to make it easier on themselves, leading to data breaches.
Because human error is so prevalent when it comes to data breaches, there might come a time where you too will experience a data breach. So what do you do then? Take immediate action! There's a step-by-step that you can follow down below so you can best protect your data and make sure that those involved are notified as soon as possible.
01. Determine what personal information has been leaked
Find out what personal data has been compromised by the breach. Was it an email address? Or perhaps confidential patient information? You also need to determine who has access to the data and who has been affected by the security breach.
02. Limit the damage where possible
Once you've figured out that a data breach has happened, make sure you limit the spread of the breach. Is there any way in which you can recall the email you've sent out or block the file attached to it?
03. Inform your CISO
Regardless of whether your data breach has to be reported to the authorities, you must report the breach to your CISO within 72 hours. They can decide whether they have to report this breach or not.
04. Inform your customers
First decide whether your customers have to be informed of the breach, a temporary loss of availability may not need to be reported. In the case that you do have to inform your customers, you should do so within 72 hours. No one likes being caught in a data breach, but as long as you respond quickly, your business can recover quickly.
05. Report the data breach
In case there's a personal data breach and it poses a risk to people, this has to be reported to the supervisory authorities of your country within 72 hours. For HIPAA, a breach or violation must be reported within 60 days.
06. Update your security training
Data breaches can happen to the best of us, but once a breach has occurred, it's important that everyone in the company is educated on what to do in case of a data breach and also what not to do.
If you've experienced a data breach, your CISO has cleared it and you don't need to report it, you can take a quick breath of relief. You've been spared of consequences other than a quick talk with your CISO (and possible more security training). But if you're not so lucky, then the consequences of a data breach can have far-reaching ramifications. This is why we think taking your time after data security breaches is bad:
-
Financial losses
-
Reputation damage
Financial cost of a data breach
The average cost of a data breach rose to 4,45 million dollars, according to IBM.
But even with that staggering average, costs can go even further. Under data protection laws like GDPR and HIPAA, a personal data breach might mean you've broken the law, which in turn opens you up to penalties and fines.
- Organizations that are found in breach of GDPR can be fined up to 4% of their global turnover or 20 million euros, whichever is the highest.
- When it comes to the American HIPAA law, violations could cost you up to $50,000 per violation with a maximum of $1.5 million per year.
Human error, therefore, becomes a costly mistake!

Reputation damage
As we all know, news travels fast! Everyone can come up with a juicy story of a data breach in recent years. Remember Facebook? It may have been a while ago, but 2019 was a wild year for Facebook in which 530 million users were affected by the breach. Usage of the platform plummeted as a result.
Of course, it's not so easy for customers to forget your data breaches either! Research has shown that up to a 70(!) percent of consumers will simply stop doing business with organizations that have been breached. Reputation damage can seriously impact your business in the long term and prevent your company from attracting new customers in the future. Reputation damage can therefore be serious enough to lead to a loss of business.

After all this talk on what happens when you encounter a data breach, it's time to talk about what you can do to prevent data breaches. After all, there's a solution for every problem, and that includes something as serious as a data breach.
First, preventing data breaches really doesn't have to be all that difficult. Because most data breaches are caused by human error, it all comes down to making sure these human errors have as little as possible chance of happening.
Most communication nowadays is digital, which turns email into a big target for possible data breaches. By choosing a secure email solution, you can pretty much eliminate a lot of the risk of data breaches.
.png)
Keep your organization free of data breaches
Download our whitepaper and learn the best practices to protect your data.
When choosing a secure solution, please pay attention to the following features:
.png?width=550&height=373&name=MicrosoftTeams-image%20(360).png)
Encryption
Encryption, and more specifically zero knowledge end-to-end encryption, is one of the biggest keys in preventing personal data breaches. That's because encryption is the process of encoding information. Only you and an authorized recipient hold the encryption key to decipher the information that has been sent out. Without that, the message will remain shrouded in mystery, and no one can access it.
Ability to recall emails
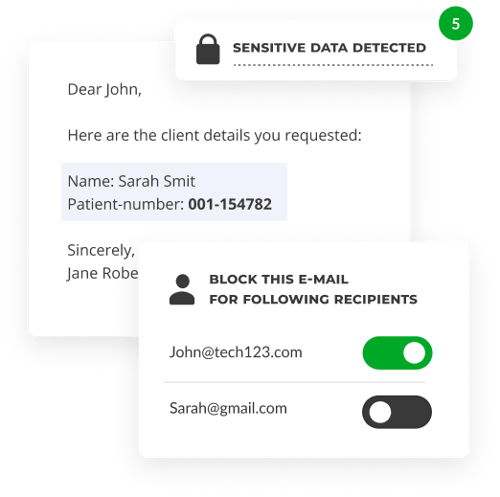
But what if you've sent an email to the wrong person anyway? You know, by accidentally clicking on your client Petra's name instead of your coworker's or by attaching the wrong file to the email, which now gains your recipient access to personal information. By choosing a secure email solution that allows you to recall emails, you can quickly retrieve the email or possibly block the file.
Increasing the awareness of your users
Human error happens because people are careless or overly busy, not because they have malicious intent. The best way to prevent them from making mistakes is to increase the awareness of your users, by having them confirm their recipients before send-off or through a content filter that picks out personal identifiable information.
.png?width=450&height=418&name=MicrosoftTeams-image%20(359).png)
Choose a user-friendly email solution
If your email security solution isn't user-friendly, then the chances are your employees will find ways to work around it. That makes your solution pretty useless! So make sure that whichever solution you choose, is as simple as possible.


With Smartlockr you choose a solution that incorporates all of the above features and more! Smartlockr allows you to send your emails and files securely while preventing data breaches through an email solution that is so simple that everyone can use it.
We do this through increasing the awareness, a seamless integration into existing work processes, and allowing you to block files even after they've been sent!
Data breaches and human error will now become a thing of the past.