"How do you take your email security?"
Okay, that’s a weird question. But let’s for a moment compare your data security to the service you get in a restaurant. And to make it a bit more specific, let’s look at the waiter tending to your needs and see how that matches up with email security.
The pop-up waiter
One waiter might delight you with extensive information about every menu item. Telling you how it’s prepared, what wine goes best with each course, perhaps they even have a nice story of the chef’s creative process. This waiter is truly committed to making sure your order is tailored to your taste buds. There isn't a single menu item that doesn't ignite a passionate ode to it from your waiter. And before you even know you need him, he's there, like a pop-up in your browser.
The result: The service may not be quick, but the experience is on point. You’ve never been more aware of the food you eat, which adds value to your evening out.
The passive waiter
A second waiter might value efficiency more. They're not wasting any time talking about food. Instead, you simply scan a QR code and your order will appear on a plate in front of you as quickly as humanly possible. You won’t see or hear from this waiter unless it’s absolutely necessary. They check for allergies and provide you with drinks, all in the most efficient way. You barely notice they are there. They do their job, but nothing more.
The result: your dinner is a procedure and not so much an experience.
 Which kind of eating experience do you prefer? The efficient or the passionate?
Which kind of eating experience do you prefer? The efficient or the passionate?
The question you might be asking at this point is what does any of this have to do with email security?
Well, let’s describe both waiters as IT professionals might:
The pop-up waiter is by far the most committed to telling you everything there is to know about the menu. In fact, merely pointing at the menu is enough for them to appear as your personal pop-up blocker.
- The upside, you’re 100% sure your order is a well-informed decision.
- The downside, pop-ups can be annoying, no matter how fancy they are.
The passive second waiter doesn’t waste any time connecting you with your food. Only when it’s unavoidable do they show up at your table for your input.
- The upside, food comes fast.
- The downside, you haven’t learned anything.
Email security comes in different styles too
In email security there are basically the same two types of waiters as in the example above. The pop-up waiter is represented by e-mail security that works as a plug-in. The second one is the passive waiter which you can compare to e-mail security using SMTP Relay Service.
Email security with a plug-in
Email security can take the form of a plug-in that prompts users to make sure the email they send has the right security settings. Using a plug-in, sending an email securely means having to take a few extra steps each time you do.
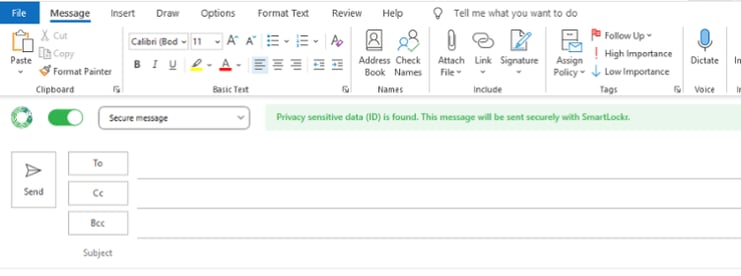
Email security in a plug-in is user-friendly, but also offers more information.
Email security in the background
The other, less intrusive form of email security, uses an SMTP Relay. Instead of asking end users to tailor the security settings of their email, people can just send their emails as they normally would. The email security is all taken care of in the background and doesn’t require any interaction with the user.
Read more about this: What is SMTP Relay Service? How does it work?
The question you are probably asking yourself now is whether e-mail security using a plug-in is better than email security in the background using?
Can e-mail security be a menu?
You may find it surprising to know that most (if not all) email security providers choose your “waiter” for you. Some email security providers only offer SMTP Relay, others will only supply you with a plug-in.
To us, this is surprising. After all, why would your email provider dictate your email experience?
We think the only good way of securing your data is your preferred way!
- One organization might favor email security in the form of a plug-in. It’s a little time consuming perhaps, but every time someone sends an email, their awareness on the subject of cyber security increases. When securing emails using a plug-in, most people become experts in the field of data security and know why and when security is needed.
- Another organization might want their email security to be as much in the background as possible, where it doesn't need any attention from the users.
And these are just the far ends of this spectrum. The reality is that every organization is different in the way they want their email security to affect their day-to-day activities. Just like everyone differs in what kind of waiter they want for their night out.
That’s why Smartlockr’s “menu” caters to your preferences. Some people like getting notified and increase their awareness in the process. Other people just like their security to be in the background where they don’t have to interact with it.
We know email security is only effective when it’s user-friendly. And what user-friendly is, is up to... well, the user.
The choice is yours
If you ever find yourself in a restaurant not liking the service, your first thought would probably to either leave the restaurant or swear never to go back there again.
If you ever find yourself looking out for email security and encounter a provider that doesn’t let you choose between a “pop-upping plug-in” or a “stealthy SMTP Relay”, then the following (free) whitepaper will be very helpful. It will make sure you get the solution you need, not the solution you’re being served.
To download the whitepaper “How to choose the right secure email solution” simply click the link below!

.webp)